Many people wonder what data the router collects on public Wi-Fi networks or in rented apartments and who can access it? We checked whether such a threat exists.
About possible data leakage due to network hacking or potential tracking parts of traffic owner router write both ordinary Internet users and experts. Such texts say that access can be obtained both to the search history and the list of visited sites, as well as to passport and other personal data. For example, in 2019 with ease The Wi-Fi network of the Sapsan high-speed trains, in which the Russian Railways company stored information about passengers, was hacked. A significant number of publications concern parental control and how teenagers bypass; whether the router stores search and browsing history, dedicated dozens of SEO articles. Separately experts note vulnerability of hotel networks, and Kaspersky Lab is extremely does not recommend use Wi-Fi points in apartments rented through Airbnb or other services.
We are all familiar with the Wi-Fi router (router) is intended for data transmission in networks of various types. In simple words, it ensures data transfer between devices connected to it and the Internet. By default, the router does not save Internet surfing history, but this is only by default. The more modern the model or firmware of the router, the more data and functions are available to the administrator of network connections launched using the device.
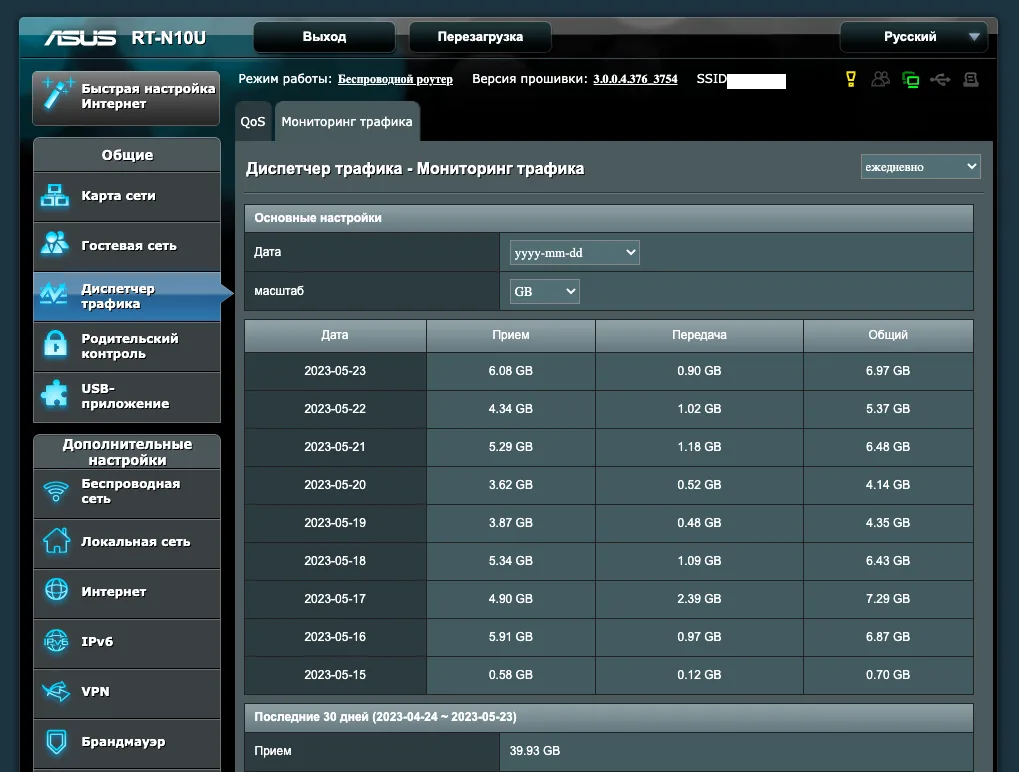
Thus, a router manufactured in the first half of the 2010s with basic firmware will most likely provide the administrator with only minimal data on the volume of traffic and will allow you to set up simple parental controls - limit the time during which Internet access will appear on the child’s gadget. Relatively new device, with 2020 firmware, will make it possible to see a complete list of pages visited during the connection.
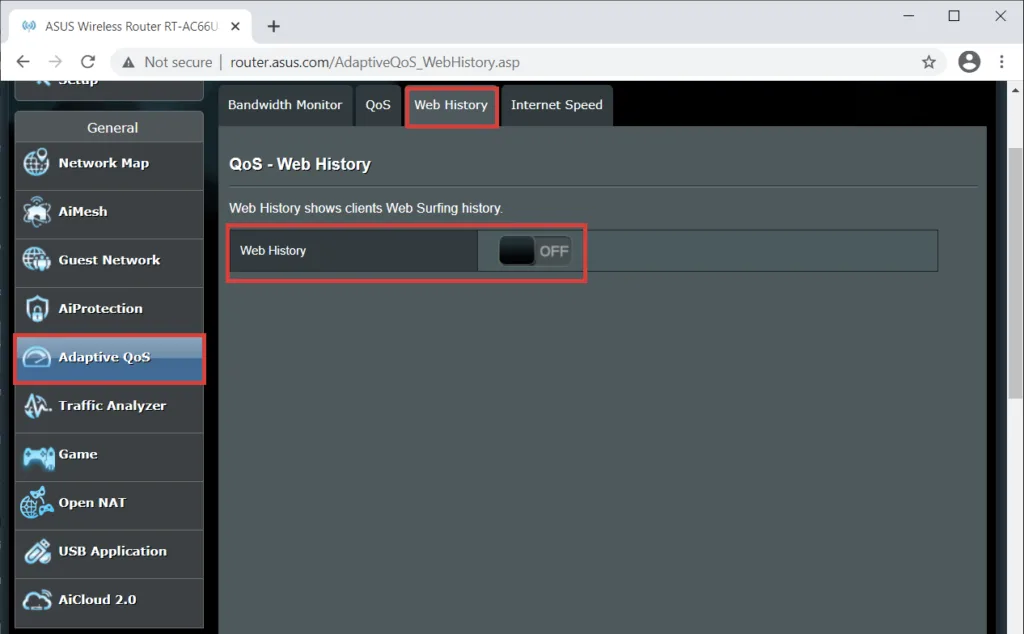
The owner of the router can get acquainted in detail with the content that was of interest to the user if he worked using the unsecured HTTP protocol (sites without a secure HTTPS connection are still not uncommon). To do this, just go to the system log. A detailed history of actions on protected sites will be inaccessible - only domains will be noted in the log, and information about what you searched on the Internet, where you bought tickets and what porn you watched is not saved by the router. Some models also allow see statistics on the most visited sites from a specific gadget. It is worth noting that the options provided by the manufacturer are mostly created for parental or corporate control and do not imply monitoring, for example, banking transactions. This information is not stored in the router log and cannot be leaked unless you click on a phishing link or unless the data transfer protocol has been changed by an attacker.
The problem with open (not password protected) and public networks is that they are often quite easy to hack: administrators do not always pay enough attention to security. So, in 2017 in Argentina there was hacked network in one of the Starbucks coffee shops, and customer devices connected to it began (without the knowledge of the owners) to mine the Monero cryptocurrency. The same goes for networks in hotels, because, knowing the network password and having the necessary equipment, a hacker can easily carry out an attack MiTM (Man in The Middle - “man in the middle”). There are several types of such an attack: for example, an attacker can create a duplicate network (a network with a name identical to the one to which the device automatically connects) or change the settings of a public access point so that traffic goes through a node controlled by the fraudster. In a MiTM attack, the attacker gains access to all transferred data, and sometimes even to data on connected devices.
Wi-Fi networks in rented apartments and apartments are also quite easy prey for hackers. When installing a router, not all owners think about the need to change the factory password or disable the ability to remotely access settings. In this situation, an attacker only needs to connect once, even to a password-protected network, and reconfigure it. As a result, if the fraudster wants, he will know everything about the insufficiently protected traffic of all subsequent residents.
Thus, widespread fears are not in vain - even you yourself can partially analyze the traffic through your home router without additional programs, let alone criminals. In fact, this is precisely what experts are warning us about: do you know who controls the network you connect to? And if not, isn't it better to use the mobile network? It is hardly possible to completely abandon Wi-Fi, but you can avoid open networks, connecting and transmitting important data without a VPN through networks in hotels, in rented apartments - anywhere where you have not configured the router yourself and are not sure of its security. When VPN is enabled, only the IP data that was assigned to you during the session will appear in the system log. It is worth remembering that this is only part of safe behavior.
Cover image: MORE ON / Pixabay
If you find a spelling or grammatical error, please let us know by highlighting the error text and clicking Ctrl+Enter.






